Be aware of undesirable user activities
Modern IT security is not only about protecting your company from external dangers, you have to be aware of insider threats too. Safetica can help you protect your data from both the unintentional and malicious behavior of your own users:
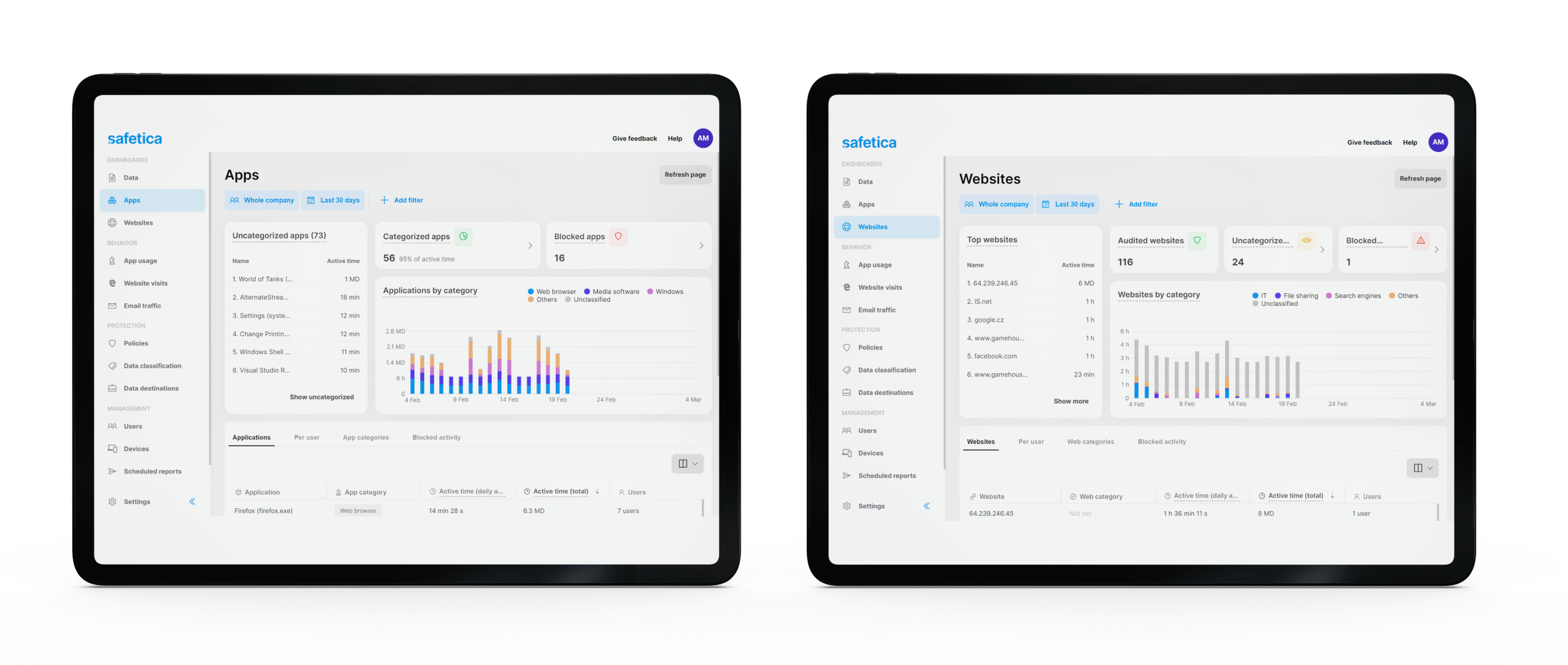
- Analyze the risk of user activities, such as file transfers, IM, printing, sending email attachments, and more.
- See what job portals your employees visit, since these might present a future data security risk.
- Utilize powerful policies to show notifications, log, or block potential risky behavior.
- Get real-time alerts and reports for blocked activities or time spent in apps or on websites.
- Control what resources can be used in your company.
- Visualize trends in user behavior.
Audit operational efficiency
Better insight into your company operations will help you run your company even more smoothly. Pinpoint troublesome elements in your processes, use your resources effectively, and address security or business efficiency concerns. Stay on top of things even when your employees work from home or on the go.
With Safetica you can:
-
- Gain a better overview of user activities on endpoints, on the network, and in the cloud.
- Display audited data in customizable reports.
- Compile forensic evidence about user activities and company policy violations.
- Get an overview of the software, cloud services, and hardware usage in your company.
- Centralize the management of BitLocker encryption to secure your data when a device is stolen.
- Get automated reports and real-time alerts on users working onsite or remotely.
Why Safetica
Continuous Monitoring and Auditing
Safetica offers real-time monitoring and audit trails that provide full visibility into data access and usage, supporting compliance and security efforts.
Zero-Day Threat Detection & Response
Safetica's proactive identification and immediate response to emerging threats ensure protection against zero-day vulnerabilities
Behavioral Analytics & Anomaly Detection
Safetica's advanced behavioral analytics identify suspicious activities and anomalies, enabling early detection and mitigation of potential security breaches.

